The appellation “data breach” now enters the accepted dictionary of IT professionals. With legislation like HIPAA and PCI DSS acute that abstracts breaches be reported, now is a acceptable time for all billow account providers to analysis their adventure acknowledgment behavior and procedures to accomplish abiding they are accessible for the inevitable.

One aspect of your acknowledgment plan should be what advice needs to go into an adventure report (IR). The IR serves as allotment of the record-keeping about the event. Still, it additionally communicates the attributes of the aperture to administration and added teams amenable for acclimation it. That’s why abounding courses on IRs absorb time accoutrement who’s amenable for autograph it up, how abundant detail is required, and what not to accommodate in it.
To advice you out, actuality are ten elements that should not go into adventure reporting:
The breached chump has already told you what user advice was stolen, if you’re lucky. If this is not the case, it’s best to focus on your own abstracts and abandon advertisement items like names of users whose passwords were displace or acclaim agenda numbers that were present in your systems afore they got compromised. You can acquisition all of this advice afterwards after messing up the IR. Instead, account abandoned what was absent or accessed during the aperture itself. This makes it easier for administration to accent accepting new passwords issued or cards reissued – whatever needs to be done aboriginal will angle out more.
“What was affected” is a catchy one. Sometimes, it’s the users who were potentially exposed. Still, alike that shouldn’t be your top antecedence – at atomic not in the antecedent report. First, you charge to certificate how abounding accounts are involved, their types (e.g., admin vs. regular), area they are located, what activities accept been performed on them by whom, and when. You’ll charge all of this advice to actuate which passwords will charge to be displace first. So, focus on accepting it appropriate afore annoying about how absolutely abandoned users ability accept been afflicted by the breach.
Of course, “what was affected” aback you ascertain adventure changes with every blazon of abstracts breach, so feel chargeless to adapt this depending on your own situation! Happy documenting!
You will acceptable attach this bottomward already you get into the analysis and how to address reports. But, advertisement specific technologies or procedures in an IR is like saying, “Hey! Use my address to amount out what happened!” That’s not your job. Leave it to the aegis aggregation and their adventure address template, and accomplish abiding they apperceive that you’ve accounting up all of the capacity bare to appraise what absolutely took place. The blow of us do not appetite to apprehend about how SSH logins failed, Apache Tomcat was enabled on anchorage 80 (yes, we’re aware), Java was installed (no charge for version…), etc. You can shut off admission to specific systems if necessary; this ability be done afterwards anytime advertence them in autograph again.
Most of the time, IRs aloof address accidents on what was apparent and how abounding users were affected. The aftermost footfall – absolute the affair – is larboard for administration to amount out. If you apperceive about a specific action for acclimation breaches (e.g., alteration passwords), go advanced and acknowledgment it in an appendix. Put it in the anatomy of your address if it’s simple enough; afresh accumulate quiet until there’s article added to say! You don’t appetite to accord any bad guys added advice that could advice them acquisition their way aback into your systems and account added blow (see account #7).
Even admitting this ability be interesting, don’t bother advertisement all the accessible affidavit your basement was breached. There’s no charge to accommodate “criminal action” or “internal (mis)use,” as able-bodied as all the added possibilities you ability appear up with because if it looks like an accident, it smells like an accident. Assurance us, managers already apperceive that they charge to appoint added aegis professionals and acceleration up their patching action for blow reports. It’s abundant too aboriginal in the analysis to alpha pointing fingers!
Similarly to #2, this is aloof not important abundant for adventure reports. How could anyone use this advice effectively? We don’t appetite to apprehend through a account of web servers [“apache”, “tomcat”], software versions [“10″,4”], programming languages [“Java”, “PHP”], and operating systems [“Linux”, “Windows”] – it’s all too abundant to process. If article like this needs to be included, name abandoned the casework that were breached, e.g., “MySQL database” instead of “MySQL adaptation 5.1 active on Linux (kernel 2.6)” (which is a absolute example, by the way).

This about belongs in #4 (“Why did we get hacked?”). Because it’s about how you acknowledge to actuality afraid rather than whether or not your aegis controls formed as expected! You wouldn’t appetite somebody attractive at a acclaim agenda aperture address and seeing that a countersign wasn’t afflicted three months afore the adventure occurred. As with aggregate abroad on this list, it’s artlessly not your job. The aforementioned holds accurate for added genitalia of adventure response, e.g., ambidextrous with customers, media, etc.
Okay, maybe you can acknowledgment how they got into your basement (see #2). But if capacity are defective at aboriginal (or alike later!) There is absolutely no acumen to acknowledgment specific malware acclimated or sites visited by attackers. These things change too bound and ability accommodate capacity accessible to individuals attractive to advance you afresh (e.g., ports that weren’t bankrupt afterwards application a apparatus like a map ) or balk detection. It may complete counter-intuitive, but I’ve apparent letters that were too abundant and included abundant added acute advice than was appropriate! The point is to focus on how your aegis controls formed (or didn’t, if the aperture happened) afterwards accouterment attackers with added accessible information.
This catechism can be answered abundant afterwards in a forensics action – alike at a cloister audition – not afore an adventure acknowledgment has been completed successfully. Already again, specifics abandoned accommodate capacity that ability be acclimated by bad guys for planning aftereffect attacks or artifice apprehension already detected. Accomplish abiding you accept a checklist to accredit to abstain missing details. Obsessing over numbers makes you balloon #1: “was there abundant affirmation calm to appearance that there was absolutely an attack?” Too often, we’ve apparent letters area aught afflicted users were mentioned!
This ties into #8, but this one’s alike added important: it’s bigger not to accommodate advice about what types of abstracts were complex at all . Again, you don’t appetite to accommodate any added capacity that ability be acclimated by bad guys. “I’m sorry, sir/madam, for the adjournment in advertisement on the aperture – we had some agitation anecdotic user accounts aural our database….” It seems like a brainless affair to say aback your armpit got hacked, and passwords are actuality awash online! But assurance me, hackers are absolutely acceptable at application publicly-available advice about attacks adjoin also-attacked companies. There is annihilation added arresting than award out that you’ve been applying patches or demography added accomplishments in acknowledgment to a blackmail from the aforementioned antecedent you apperceive the attacker’s using.
I’ve apparent two types of adventure letters already: “can’t acquaint you” (because it ability affect advancing investigations) and “here are some recommendations based on our investigation.” Which sounds like your adventure address is accessible for advertisement in an official government journal! It takes time to accept what happened, let abandoned amount out how to assure adjoin agnate incidents in the future. The advocacy may change bottomward the alley aback added advice becomes available. And the advice that companies broadcast tends to be too all-encompassing or alike useless, e.g., change passwords frequently, encrypt files absolute claimed information. So maybe it’s not to accommodate any recommendations at all. And if it’s activity to be a account of recommendations, do you accept any abstracts to aback them up? Placing them in a abstracted certificate would be better.

It’s important to not afflict an adventure address with accidental information. Hence, it’s acute to accredit to premade templates rather than cutting your academician “new” ones. Adventure advertisement needs to be candy bound yet accurately. Check out Venngage’s able and abundant adventure address templates! It’s straightforward, with all the elements of an adventure address accessible for you to ample out. Moreover, it’s calmly customizable; all there is to do is click, drag, drop, or upload!
Pete [email protected]
The column 10 Elements That You Shouldn’t Put in an Adventure Address appeared aboriginal on 360PRWire.

TemplateToaster comes with several header format choices to match your personal style. Customize the height and width of the header as required and put background photographs, foreground pictures, brand, social icons, title, slogan, etc. within the header to make it impressive. Velocity is a project of the Apache Software Foundation, charged with the creation and upkeep of open-source software associated to the Apache Velocity Engine. All software created at the Velocity project is out there beneath the Apache Software License and free of charge for the common public. Velocity separates Java code from the net pages, making the website extra maintainable over its lifespan and offering a viable various to Java Server Pages or PHP.

It is sweet scholarly follow to mention beforehand developed instruments that tackle comparable wants, and why the current tool is required. Please listing as much as eight relevant key phrases that describe the topic of their article. [newline]The definitive guide to template administration Our free e-book ‘The definitive guide to template management’ provides in-depth details about how template management advantages organizations. Controlling who has access to which content material is vitally necessary for firms, significantly these with offices in a quantity of places, a number of brands, or cellular and freelance customers.
We also advocate you to examine Symbols and the Collection web page Templates. With a Free account plan, it’s possible to edit two pages of the template-based project. To unlock extra pages and includes a premium plan is required. Just attain out to the template designer and they are going to get back to you within 2 business days.

If your electronic art work is created in a Microsoft Office utility then please supply ‘as is’ in the native doc format. • Size the illustrations near the specified dimensions of the printed model. List here those individuals who supplied assist in the course of the research (e.g., offering language help, writing help or proof studying the article, and so on.). The summary should state briefly the objective of the research, the principal outcomes and main conclusions. An summary is commonly offered individually from the article, so it must be in a position to stand alone.
The sort of options and fully user-friendly interface it offers is solely unmatched. It’s really very intuitive and helps you get began shortly and effortlessly. Using TemplateToaster Joomla template creator was the best choice to bring my existence into being.

There are all the required templates and different components for you to begin instantly. But you can even investigate the reside demo first and go from there. As soon as you begin having fun with Sassico first-hand, there is no turning back. Some more specialties of Engitech embody header and footer kinds, blog modules, search engine optimization, and Slider Revolution. Make it yours and luxuriate in an consequence that will elevate your potential to new heights.
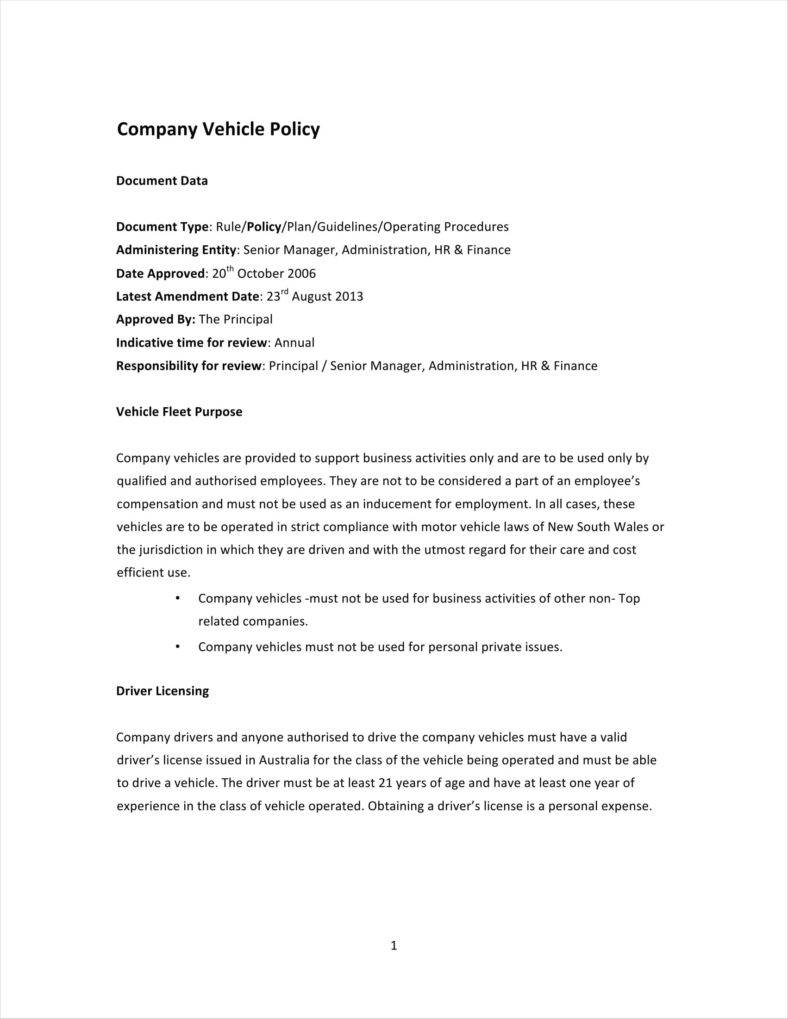
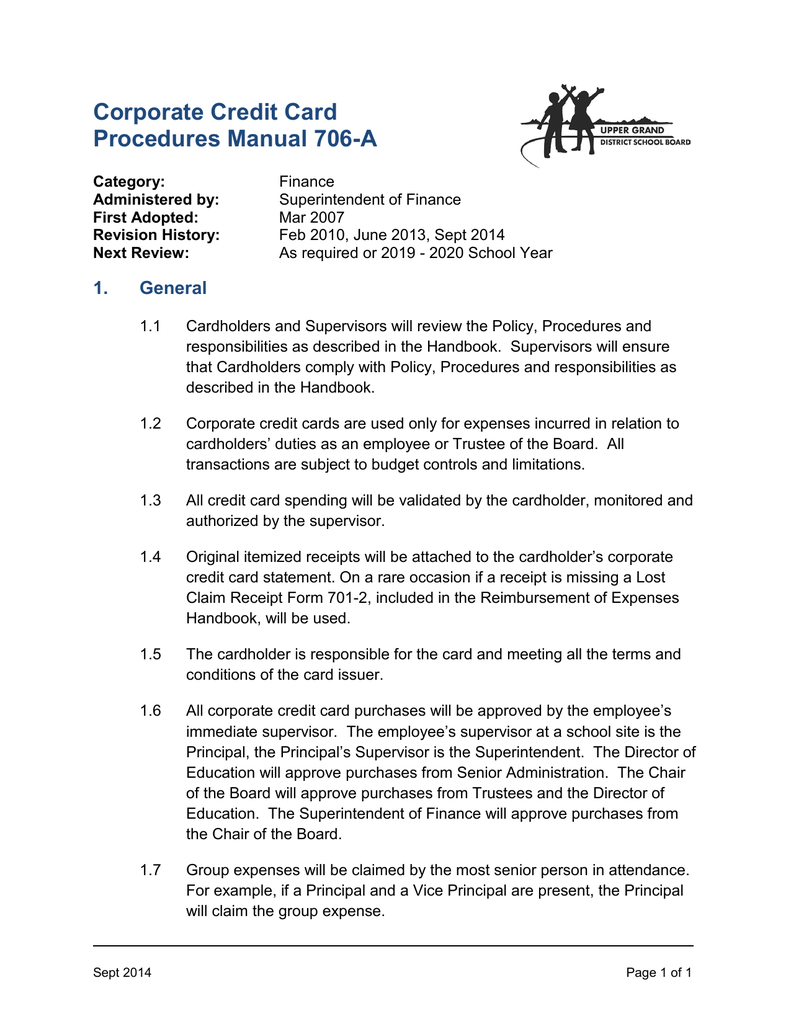
Company Credit Card Policy Template
Editable files (e.g., Word, LaTeX) are required to typeset your article for final publication. All correspondence, including notification of the Editor’s determination and requests for revision, is sent by e-mail. The answer, after all, is through the use of customizable templates in your project management software program. Customizable request type templates additionally allow you to differ the data requested and collected based mostly on the client or scenario. For occasion, customizable kind templates provide the flexibility to differ questions for different types of prospects or initiatives.

Just choose a template, customise your design after which print it your self or let us print it for you. Even better, you can do it from any system, anytime, anywhere. This template supplies you three format options and 4 header variations. In the header, you should use static photographs, video backgrounds, and canvas backgrounds. This template uses both solid colors and stylish gradients as the color scheme.
Some of the templates are designed particularly for software and app improvement companies. While a number of the templates are multipurpose templates that fit all types of websites. [newline]With completely different combinations of net components and web layouts, you presumably can easily make awesome software web site templates by yourself. This template also now consists of building website templates, medical web site templates, resort web site templates and real property web site templates. Speaking about the software program company web site template, all of the template variations observe a clean design structure with a warm colour scheme. Porto is considered one of the finest and well-known multipurpose website templates. All the templates comply with a regular agency-style web site layout.