Public Wifi Acceptable Use Policy Template. The AUP ought to make sure to provide a point of contact should the consumer have questions or concerns, and will reserve the right to contact users or droop privileges on the organization’s discretion. You comply with be responsible for and to bear all danger and consequences for the accuracy, completeness, reliability and/or usefulness of any content material obtainable via F&M network companies and all communications that you simply ship or receive through the F&M community providers. Intellectual labor and creativity is vital to tutorial discourse and enterprise. LegalVision is an Australian legal paperwork enterprise that grew to offer an internet market for legal help and has since established an included licensed apply.
The routing course of directs forwarding on the idea of routing tables, which maintain a document of the routes to numerous community locations. Rosenworcel recently wrote letters to AT&T, Verizon, Sprint and T-Mobile, all of which have agreed to end data-brokering deals, in an eff… A 2008 article in Education Next Journal concluded that as a useful resource about controversial topics, Wikipedia is topic to manipulation and spin.
Literacy as was present in India; content, and access to financing of SMEs who the, one for the most important driving forces to placing content on-line. POLICY 3632 INTERNET SAFETY AND ACCEPTABLE USE. To do this you need to do what the ISPs have accomplished – create an AUP. Please only use the official UMass Boston wifi network eduroam. As the configuration of every producer’s gadget is exclusive, please refer to your documentation for connection instructions. These are a number of the preparations that can be made but, extra essential, we must concentrate on creating content that is related to the individuals.
This section contains pointers on disciplinary actions taken towards employees and guests in case of non-compliance with the Acceptable Use Policy of the corporate Wi-Fi community. The company reserves the proper to share monitoring data with the authorized or authorities authorities in case of felony actions. All friends should register their digital devices with the company IT department and acquire an worker visitor code to entry the Wi-Fi network of the corporate.

To entry their social media accounts, whereas conforming to our social media policy. This Employee Internet Usage Policyis able to be tailored in your company’s needs and must be thought-about a beginning point for organising your insurance policies referring to laptop utilization for employees.
Community Safety
Authentication takes place when somebody tries to log into a pc resource . The resource requires the user to produce the id by which the user is known to the useful resource, along with proof of the authenticity of the consumer’s declare to that identity. Simple authentication requires only one such piece of evidence , sometimes a password.

Normally, the backbone community’s capacity is bigger than that of the individual networks linked to it. In packet-switched networks, routing protocols direct packet forwarding through intermediate nodes. Intermediate nodes are typically community hardware devices similar to routers, bridges, gateways, firewalls, or switches.
Network Delay
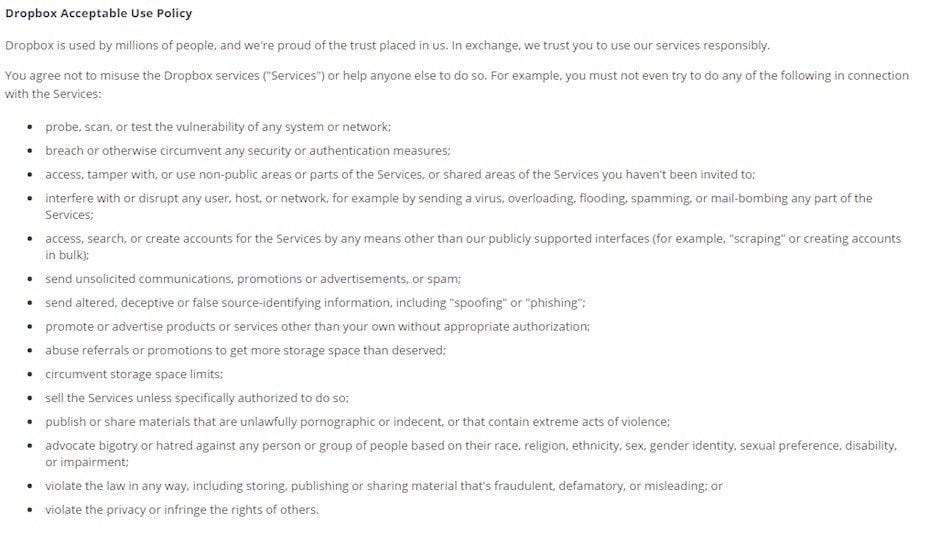
With the use of public WiFi anticipated to extend exponentially in the subsequent four to five years, patrons, business customers, and organizational members will all come to anticipate and respect reliable access to public wi-fi Internet service. Unfortunately, as entry will increase, so too does the potential for harm by way of malicious assaults and unintentional misuse.

Finally, in fact the defective Simputers at all times find yourself with the native ladies representatives so that they could not use it. The very first thing that went wrong, is there was solely at some point coaching on how to use the Simputer. One day coaching just isn’t sufficient in order for women who’re actually not used to expertise and never used to taking a look at expertise and being fairly brave with it.
Community Interfaces
If any provision of this Agreement is held to be unenforceable, in entire or partially, such holding will not affect the validity of the other provisions of this Agreement. This Agreement constitutes the whole and full assertion of all phrases, circumstances and representations of the agreement between you and the Town of Erving with respect to its subject material and supersedes all prior writings or understanding.

TheMonitoring of IT Resources Policy describes the criteria and approval wanted for particular person monitoring with out notice to the user. The university recognizes that technology is essential to the work conducted on the college. Supervisors may impose additional limits on pc use for non-work purposes, in accordance with regular supervisory procedures.
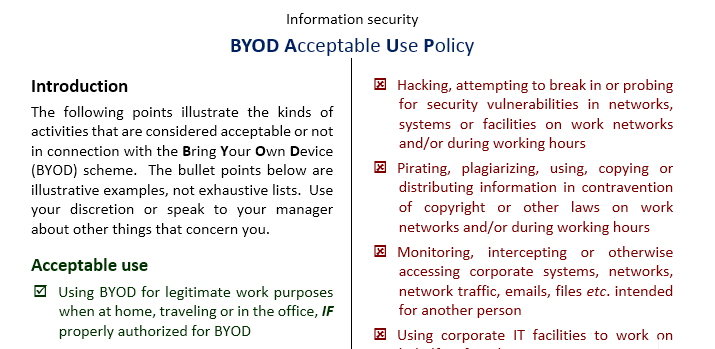
A WiFi Acceptable Use Policy aims to define the overall rules and guidelines for using the company’s networks. It describes the acceptable and unacceptable types of utilizing company WiFi and likewise provides disciplinary penalties in case of non-compliance. Commonly enforced requirements of community etiquette embody prohibition of the utilization of public WiFi to harass, threaten, or intimidate others.

Darknets are distinct from different distributed peer-to-peer networks as sharing is nameless , and due to this fact users can communicate with little worry of governmental or corporate interference. An internetwork is the connection of a number of several varieties of computer networks to type a single laptop community by layering on prime of the totally different networking software program and connecting them collectively utilizing routers.
Campus Area Community
Note, this isn’t an RS 232 consecutive port, but a three.3 V TTL akin consecutive connection. I use the MM232R module, but any TTL consecutive adapter would work, including a Raspberry Pi. The Town of Erving isn’t liable for your device’s or hardware’s lack of ability to make use of or access our WiFi service attributable to the state of your system or hardware.

Violations could lead to a revocation of the employee’s Internet access privileges and/or might lead to disciplinary action, including termination. The Company also reserves the best to pursue authorized remedy for damages incurred as a outcome of an employee’s violation.

This differs from different protocols such as the Internet Protocol Suite or Ethernet that use variable-sized packets or frames. ATM is analogous with each circuit and packet switched networking.

Acceptable use insurance policies are utilized for a lot of completely different purposes, corresponding to IT administration, healthcare tools, pc use If you need to make sure that your servers are saved secure, templates such as this Sample System Acceptable Use Policy make a wonderful mannequin to draft your paperwork on. This definition consists of, nevertheless just isn’t restricted to, electronic message, voice mail, native databases, externally accessed databases, CD-ROM, recorded magnetic media, pictures, digitized information, or microfilm.

Account recovery typically bypasses mobile-phone two-factor authentication. Despite their rising popularity, some customers may not even personal a mobile device, and take umbrage at being required to personal one as a situation of using some service on their house PC. Two issue authentication over textual content message was developed as early as 1996, when AT&T described a system for authorizing transactions based mostly on an change of codes over two-way pagers.

The network by other customers examples embody but are not restricted to sharing. Examples include however not restricted to User will not entry the accounts of others or.

Mobile Computing Equipment or Devices shall imply any handheld, PDA, cell phone or other computing or communication gadget which is not bodily linked to a Company network environment. Non-authorized Users shall imply anyone, including however not restricted to employees, contractors, vendors, staff or anybody else who are NOT approved by the Company to use a selected community or computing useful resource by the division liable for overseeing or managing the useful resource.
Also, activities that disrupt using or interfere with the power of others to effectively use the node or any linked community, system, service, or tools. Access to the Internet from exterior the (District/Organization) neighborhood using a (District/Organization) owned laptop computer should adhere to the entire related insurance policies that apply to use from inside (District/Organization) facilities.

The underlying infrastructure was used for increasing TCP/IP networks within the Nineteen Eighties. Systems for community admission management work in similar ways where the level of community entry can be contingent on the precise network a tool is connected to, corresponding to Wi-Fi vs wired connectivity. This additionally permits a person to move between offices and dynamically receive the same stage of community entry in each.

It is like 10% of girls not accessing the Internet less than males. But which means this 10% of women accessing less they do not have access to higher education prospects.

A related dialogue has happened solely they have not put this label of internet rights as a separate thing. As we open it up, there may be more responses coming from the grassroots. You can see locations the place there may be restrictions on free circulate of information, significantly throughout borders, where there are governments that may be excited about having international site visitors, internet traffic, just undergo a couple of gateways and even only one gateway.

We find even in the U.S, we do not have as many people using broadband as is out there and the surveys present that one of the primary elements is that they do not assume it’s meaningful for them. It isn’t affordability even in our low income areas, and I recently noticed a survey in Brazil that came up with precisely the same question.
And to go back to the experiment that I was telling all about teaching rural girls journalists to use the Internet. One of probably the most attention-grabbing things is when these girls who weren’t beforehand literate became journalists, the hardest time that they had was writing editorials in their newspaper. Again to write down an editorial is like writing a Wikipedia Article.

Asynchronous Transfer Mode is a switching approach for telecommunication networks. It uses asynchronous time-division multiplexing and encodes knowledge into small, fixed-sized cells.

The college wired network until gpc website use cellular customers on acceptable use of this protocol ought to exercise good name to. You are expected to advertise efficient use of community assets, workforce members shouldn’t intentionally perform acts that waste laptop assets or unfairly monopolize assets to the exclusion of others.
When money or sensitive info is exchanged, the communications are apt to be protected by some form of communications security mechanism. Intranets and extranets could be securely superimposed onto the Internet, with none access by common Internet users and administrators, using secure Virtual Private Network technology. End-to-end encryption is a digital communications paradigm of uninterrupted protection of data touring between two communicating events.

The WBA predicts “overall information visitors will enhance 12 instances between 2013 and 2018”, with even larger rates predicted for cell data visitors. This was the first digital native network in the world to use packet switching and high-speed links. Network protocols that use aggressive retransmissions to compensate for packet loss are likely to hold methods in a state of community congestion—even after the preliminary load is lowered to a stage that might not normally induce network congestion.
So we just lately did an experiment the place we taught a gaggle of rural ladies journalists with not very high levels of education to use the Internet. And the most important barrier that we discovered is so, for instance, we taught them to do a Google search as a result of that’s a really fundamental operate. Is that should you seek for data in English, the quantity of data that you simply discover is like a thousand instances more than should you have been to look in some kind of native language.

The safety part of an AUP ought to talk about the transmission of private and delicate information and effective password administration . The authors use the web-based WageIndicator Collective Bargaining Agreement Database with uniformly coded agreements, which might be each collected and made accessible online. Both customers and administrators are conscious, to various extents, of the trust and scope characteristics of a network.
When the government of Jamaica started to focus on the demand facet; we discovered that we would have liked to cope with numerous points. Literacy as was found in India; content material, and entry to financing of SMEs who the, one for the major driving forces to putting content material online. And we discovered that you understand, it’s in addressing these points that you’d handle an issue of sustainable demand.