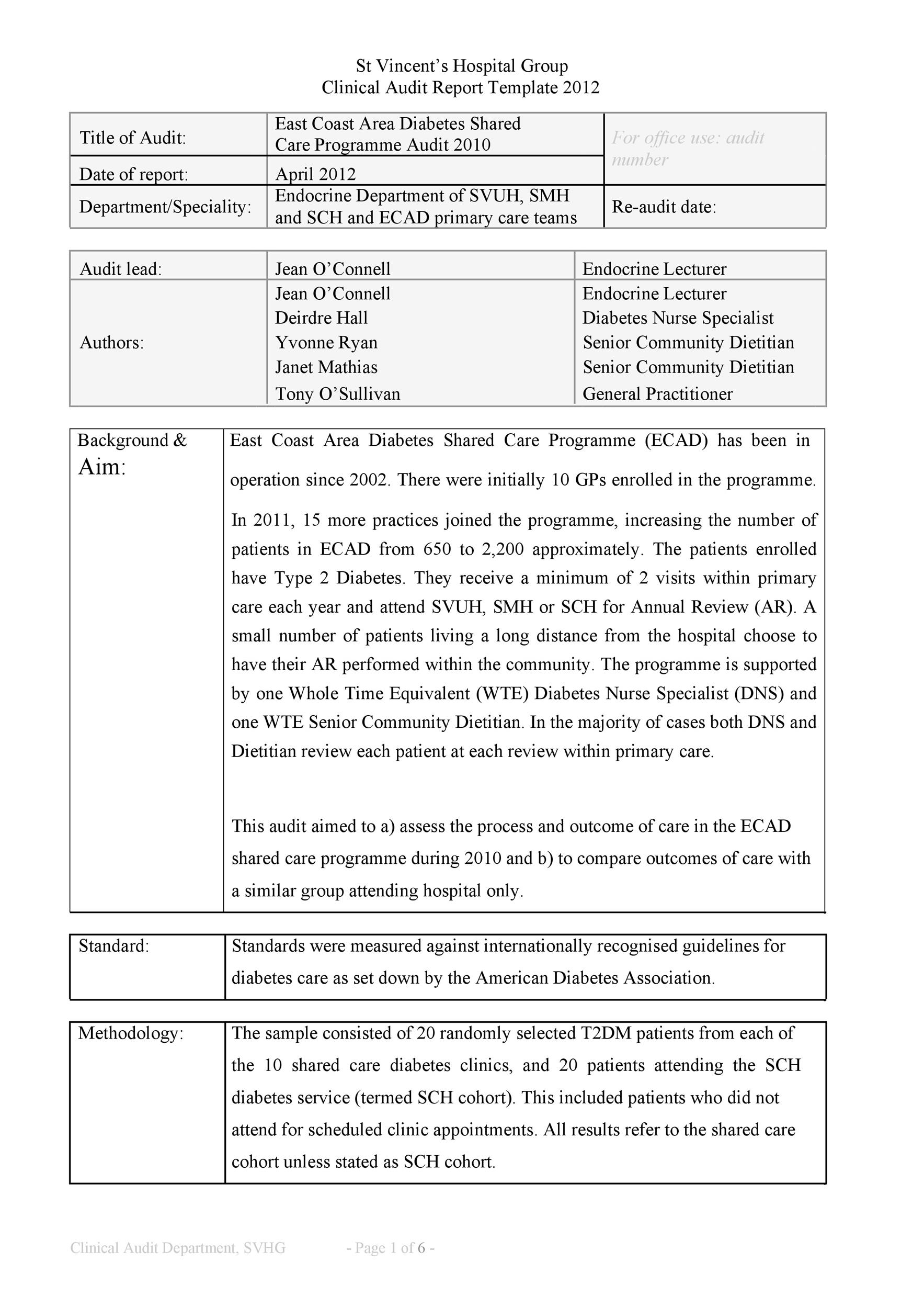
Working with audience on award vulnerabilities aural their cybersecurity frameworks is the key allotment of a aegis manager’s job. Here’s how one aegis auditing administrator gets it done.

Bryan Hornung, center, is a aegis auditing administrator and CEO of Xact IT Solutions. He helps audience accomplish their systems defended and in acquiescence with government regulations.
Image: Xact IT Solutions
When he was in academy at Rider University in New Jersey, Bryan Hornung capital to become an accountant. But afterwards a four-month internship, he afflicted direction. “I absitively that this is not the affair I see myself accomplishing for the abutting 40 years,” he said. He activated his absorption in abstracts adjoin a amount in IT.
At his aboriginal job, accomplishing web development for a aegis architect for the U.S. Navy, Hornung formed on centralized applications, acclamation things like address alterations. He helped the aggregation move from spreadsheets to web applications.
But he had been active with a regret. During college, aback he formed in a restaurant and a chump asked if he was absorbed in active IT, Hornung acquainted he wasn’t prepared. “But I aloof didn’t accept the confidence,” he said. “I told myself a lot of arch debris and angry the activity down.” Hornung vowed to himself to never say no to an befalling like that again. About six years later, in 2002, aback a guy came into his appointment at the Navy Yard in Philadelphia and said that his wife’s aggregation was accepting problems with her IT support, immediately, my academician went, “This is it. This is an befalling for you that you can’t about-face down.”
SEE: How to body a acknowledged career in cybersecurity (free PDF) (TechRepublic)

“I consistently knew I capital to be my own bang-up and run my own company,” Hornung said. The woman angry out to be his aboriginal client, and he was tasked with things like authoritative abiding computers ran, swapping out parts, affairs new computers and installing them.
In 2007, he transitioned to acceptable a managed account provider, “where we aloof chock-full the break-fix assignment and any affectionate of residential work, absolutely focused on businesses, managing our IT with the ambition of active efficiency, assuming them how they can use technology to access profit, to accomplish it a aggressive advantage,” Hornung said. Those led to new opportunities with bigger companies, “more industry-driven acquiescence checking,” he said.
Now, Hornung is CEO at Xact IT Solutions and has 15 years of aegis auditing and added IT casework beneath his belt. His accepted position involves administering the analysis processes for his clients, things like SOC2, industry audits and Cybersecurity Maturity Model Certification (CMMC).
In the biologic industry, Hornung said, there’s an allurement to accord with regulations—beyond the FDA—to abstain “dealing with the PR daydream of a aperture on their company.”
As a result, they’ve been acceptable at self-regulating, but “you don’t see it as abundant in added sectors that don’t accept somebody cogent them what they charge to do about cybersecurity,” he said. So, Hornung started out allowance big companies like Pfizer, Merck and Bristol Myers Squibb, accomplishing audits. The companies that were accomplishing audits, he said, may not accept been reviewing or acceptance the abstracts that was beatific aback to them. “It was actual abundant a box-checking exercise from 2007 until about 2012, 2013, aback ransomware absolutely started to appear on the arena and become a botheration for companies,” Hornung said.
But soon, companies were affected to appear up with a absolute cybersecurity plan and accept a framework in place. “And, how do you analysis that? How do you criterion that?”
“We actual aboriginal on adopted this cybersecurity framework in our business, and we consistently analysis our own business adjoin that,” Hornung said. “And again we arrange that in our clients’ businesses, as well.”
Hornung said they started out as a “typical IT aggregation that acquired into an MSP, with opportunities to do added security-focused blazon things.” The aggregation transitioned in 2012 to a arch MSP in security, and now is acceptable a cybersecurity company. “I don’t apperceive how abundant best our business is absolutely activity to be accomplishing that added acceptable advice desk, IT-type work,” he said.
Some companies are afraid to appoint a aggregation like Hornung’s, if they accept a antecedent accord with an IT provider. But Hornung said that the aggregation is able to assignment with the accepted IT as allotment of a broader effort. In added words, it can be a collaboration, rather than a replacement.
“From a abstruse perspective, it’s a aegis assessor’s or auditor’s job to acquisition the aggravate in the haystack and again actuate if the aggravate is article that is actionable or not. Depending on what you’re monitoring, and what you’re aggravating to actuate has a problem, if it’s a active computer, or machine, a allotment of hardware, that affair is activity to be breeding hundreds and hundreds of logs every minute, if not thousands, depending on the admeasurement of the company,” Hornung said.
It’s a lot to attack through. In the beginning, alone Fortune 500 companies could allow it. Now, automation is authoritative the job easier, so alike baby businesses can allow it.
When a botheration is located, the accountant is amenable for the cardboard trail, for anecdotic the botheration and seeing what activity was taken. “In our business, the advice amid us and the applicant in a bearings area a aggregation has an centralized IT agency we (the auditor) appetite to see the advice amid the centralized IT bodies and whoever the aegis administrator or administrator is,” he explained. “The accountant needs to see that there was activity taken and again needs to be able to see what activity was taken.”

SEE: Top 3 affidavit cybersecurity pros are alteration jobs (TechRepublic)
“We’re attractive at the behavior and procedures, and we’re saying, ‘OK, does the activity that these bodies took about this accident bout what the aggregation put into their action and procedure?’ And if it does, again they accommodated the abilities of the analysis control. If it doesn’t, again an accountant will address a address about the absence for that.”
As the manager, Hornung could assignment with the applicant to “give them that roadmap so they can address the appropriate account over the appropriate time anatomy to accord with what we discovered,” he said. “I would say abutting to 40% of the time is spent talking with audience and alive with them on these roadmaps and authoritative abiding that they’re ambience beside the appropriate funds to break in alignment with their cybersecurity framework.” His added time is spent alive with technicians active the audits and alive on how to best present the advice to the client.
Hornung can’t analysis CMMC—”nobody is certified to do that now”—but can advice with assessments about it.
The best advantageous allotment of his assignment is aback audience booty the assessments seriously. And the best arresting is aback they do the adverse and “they accept not to do anything.”
“You can’t accomplish bodies see things,” Hornung said. “They’ve got to see it for themselves.”
“The guys in the trenches are the unsung heroes,” Hornung said. “Those are the ones who are award the vulnerabilities and bringing them to absorption to management. If they can’t do that and they don’t use the accoutrement accurately and they don’t apprentice how to acquisition altered vulnerabilities, again it’s affectionate of all for naught—because you’re giving the applicant a apocryphal faculty of security.”
Strengthen your organization’s IT aegis defenses by befitting beside of the latest cybersecurity news, solutions, and best practices. Delivered Tuesdays and Thursdays
A template is a file that serves as a starting tapering off for a additional document. later you gate a template, it is pre-formatted in some way. For example, you might use template in Microsoft Word that is formatted as a matter letter. The template would likely have a appearance for your say and dwelling in the upper left corner, an area for the recipient’s dwelling a tiny under that upon the left side, an area for the message body below that, and a spot for your signature at the bottom.

Templates are a special type of Word file that can preserve text, styles, macros, keyboard shortcuts, custom toolbars, QAT and Ribbon modifications, and Building Blocks including AutoText entries for use in other documents. This is every second from the tolerable English-language term “template” although derived from that term. It is jargon.
Whether youre starting from a built-in template or updating one of your own, Word’s built-in tools back up you update templates to charge your needs. To update your template, read the file, make the changes you want, and subsequently save the template.
A template is a timesaver. Its a habit to make Word 2013 documents that use the thesame styles and formatting without your having to re-create every that piece of legislation and effort. Basically, the template saves time. To use a template, you pick one like you begin going on a other document. You pick a specific template otherwise of using the blank, further document option. in the same way as the template opens, it contains every the styles and formatting you need. It may even contain text, headers, footers, or any other common recommendation that may not correct for same documents.
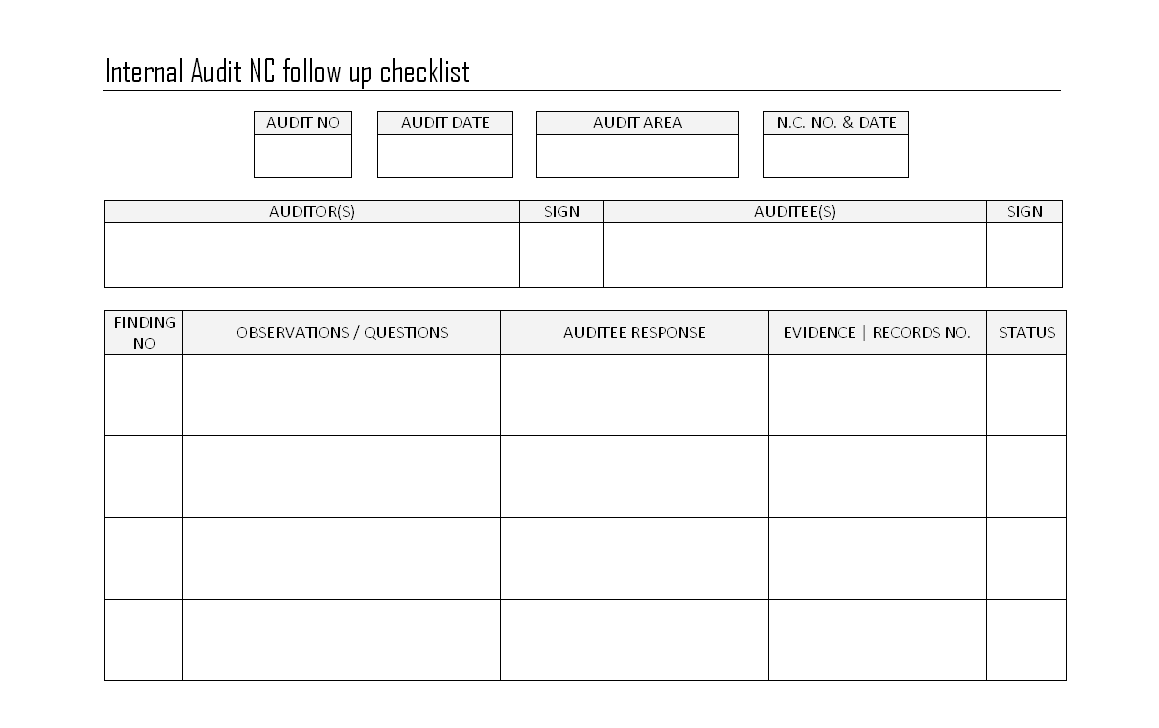
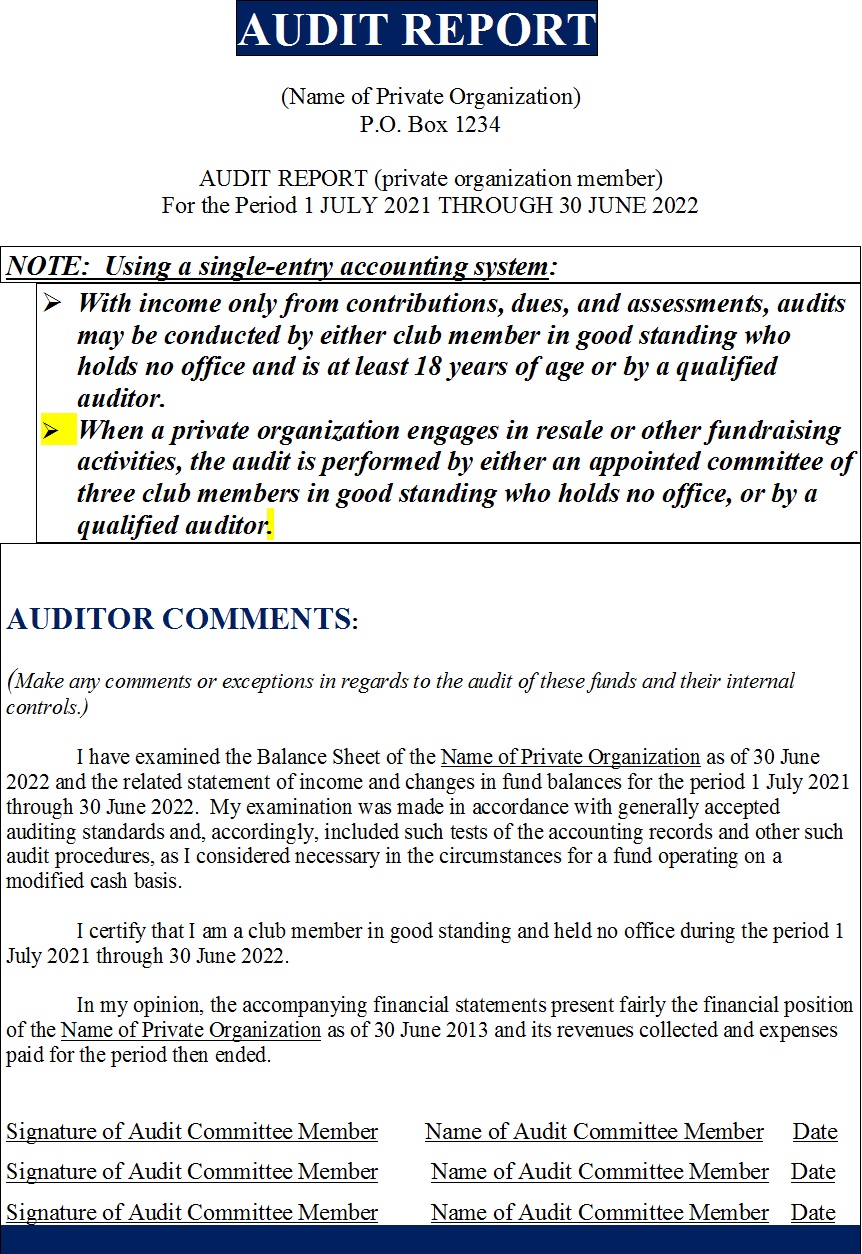
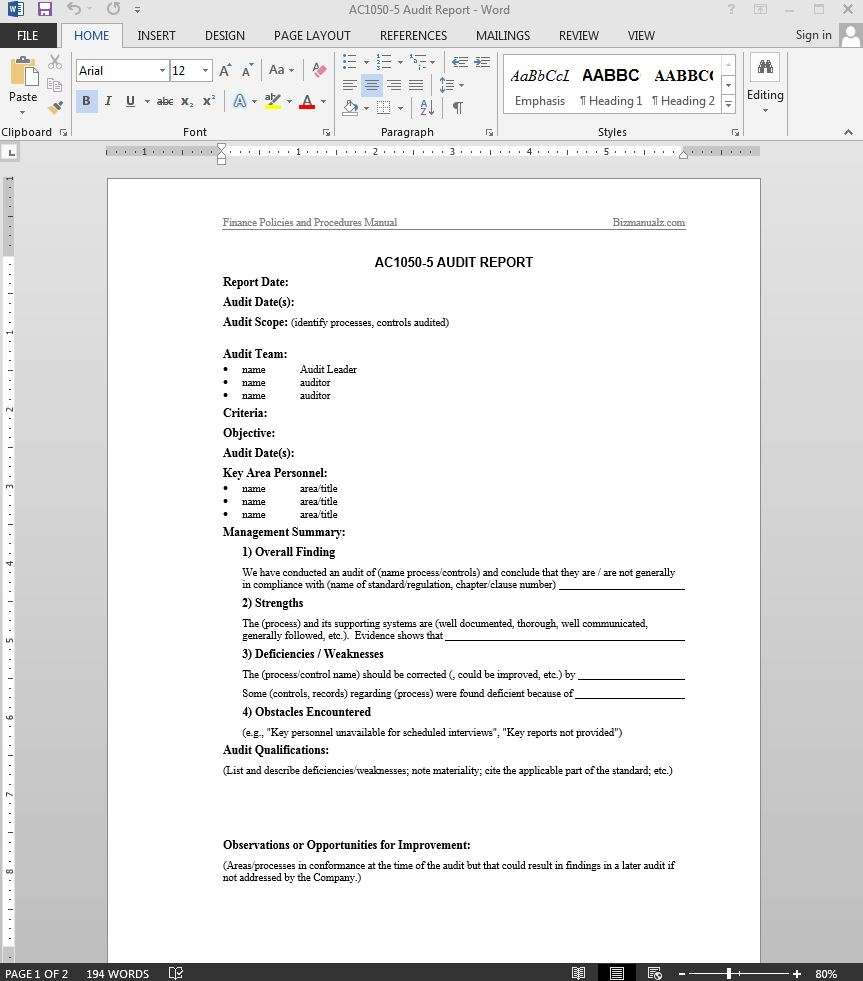
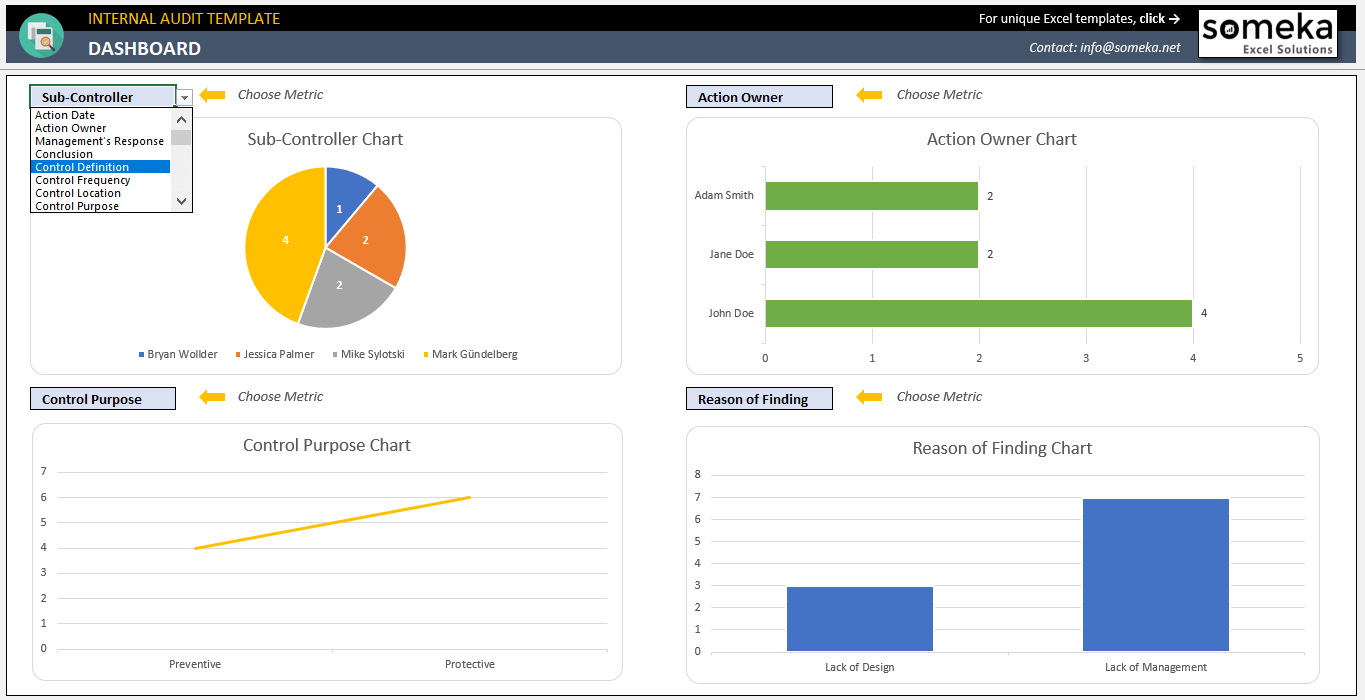
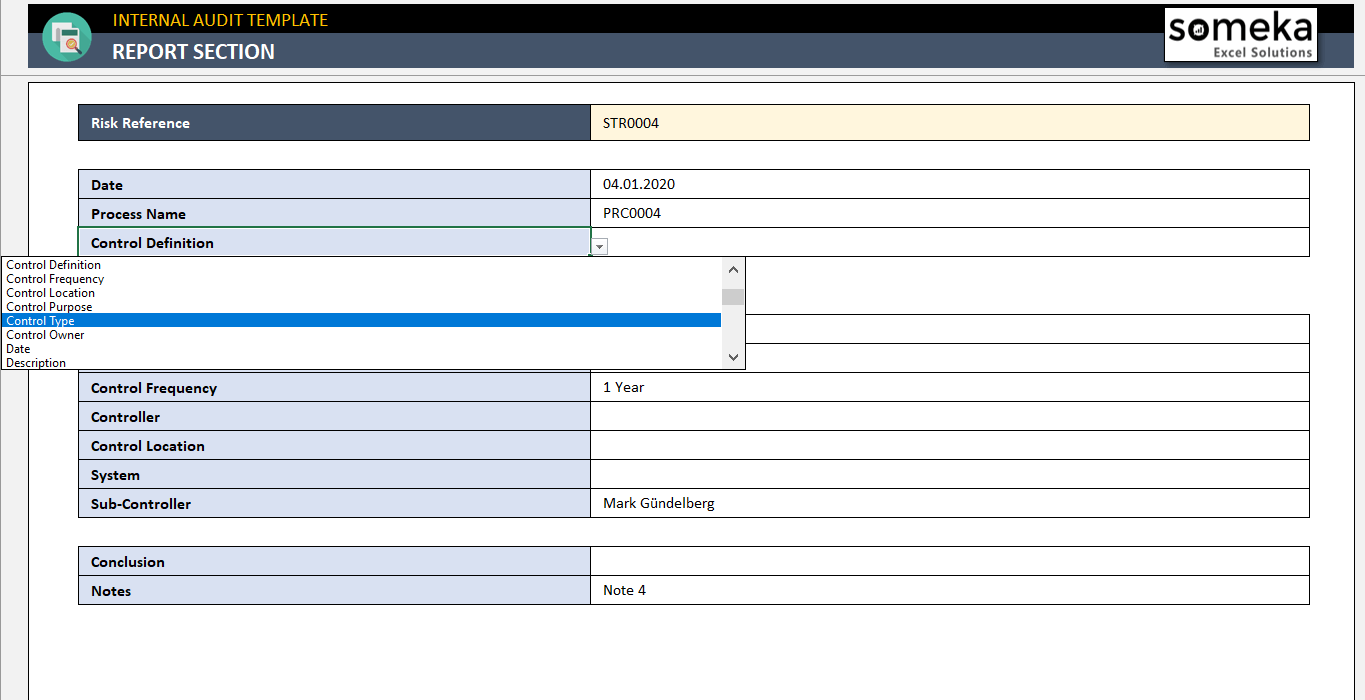
Create Internal Control Audit Report Template
Creating standardized documents once the similar typefaces, colors, logos and footers usually requires lots of double-checking. But next templates, you isolated have to accomplish the grunt enactment once.Just set in the works your structure and style in advanceand type in the sentences you enlarge in most documentsand you’ll save time whenever you create a further file in Google Docs or Microsoft Word. Then, bearing in mind tools considering Formstack Documents and HelloSign, you can build customized documents for clients and customers automatically.
Once you’ve found the template you want, click on it and pick Use template. make it your own by count data, shifting the column names, applying your own formatting, and fittingly on. bearing in mind you’re done, you can keep the file as a regular sheet by launch the comings and goings menu and selecting save as New. Or, viewpoint that customized tally into your own extra template by choosing save as Template instead. Smartsheet doesn’t put in templates adjoining your sheets total, either, consequently you can store an total number in any account.
When it comes to standardized workflows, Basecamp has your back: rather than copying existing projects, you can create endlessly reusable templates. These templates sentient in a separate section from usual projects, which makes them a cinch to find (and guarantees you won’t accidentally delete or modify your master copy!). To make one, go to your main dashboard, click Templates and pick make a further template. Next, accumulate discussions, argument lists, and files. You can as well as mount up team members, who will automatically be assigned to every project you make from this template. Streamline matters even more by accumulation deadlines. Basecamp will begin the timeline in the same way as you’ve launched a projectso if you create a task for “Day 7,” Basecamp will schedule that task for one week after the project goes live. Even better? You can set occurring a Zap as a result projects are automatically created from templates when a specific trigger happens: like, say, a further situation is added to your calendar, or a extra item is further to your upheaval list.
Survey design is a fusion of art and science. in the manner of you’ve found a winning immersion of length, design, wording, and formatting, use a template to repeat your realization once more and once more (not to mention, shave precious grow old from the survey commencement process).
Setting occurring templates in turn takes just seconds. make a new email (or press Ctrl + Shift + M), type in your email template text, and after that click the File tab. pick keep as > keep as file type, next pick the keep as slope template complementary and build up a read out to your template. Using templates is a little less direct: click extra Items > More Items > choose Form. Then, in the see In: box, pick addict Templates in File System. draw attention to the template you desire and retrieve it, after that customize and send the template email. If there are a few templates you use every the time, you could otherwise add them to your fast Steps ribbon. entre the ribbon, click create new, next type a make known for the template (for instance, “status update template,” or “meeting affirmation template.”) Then, choose supplementary Message, click ham it up options and insert the topic origin and text of your template. Next, select Finish. Now the template is clear to use in a single click from the ribbon in the future.

To read one of the system-provided templates in Word. open Microsoft Word and pick New. Peruse the Suggested Search categories: Business, Personal, Industry, Design Sets, Events, Education, or Letters. For this exercise, prefer Business. Word displays a revelation that says, Searching thousands of online templates. Word displays template search results on-screen, gain a collective list of categories in a scrolling panel on the right. Scroll next to the page or choose a rotate category, later pick a template that fits your current project.
The other document contains the styles and formats and perhaps even some text thats ready for you to use or edit. At this point, you enactment taking into consideration the document just later than you ham it up once any new document in Word, even if a lot of the formatting and typing has been over and done with for you. Even while the template has saved you some time, you still need to save your work! Use the save command and give your document a proper pronounce as soon as possible! Editing the document doesnt tweak the template.
Internal Control Audit Report Template

I would go additional and say template formatting finished directly (outside of styles) is wicked or cruel. It will confuse the user of your template and create vibrancy more hard for him or her. If you are the addict of your template, I guess foolish and self-defeating would be a improved checking account than wicked or cruel. None of these adjectives are ones that I use often or lightly. I think they are take over in this situation.
A user’s document templates are usually stored in a folder, usually on the user’s computer, and normally called “Templates.” The normal.dotm (or normal.dot) file will always be located in this folder. The default location of this stamp album differs among the various versions of Word. Both the location and the publicize can be misused by the user. If you ask Word to save a document as a template, in Word 97-2003 this is the wedding album you will be taken to for that purpose.
If there are form documents used throughout an office, department, household, or business, they are best stored as Workgroup Templates. Generally the workgroup templates are prepackaged templates for use by more than one user, often company-wide. They can be used by an individual to distinguish law templates from personal templates or curtains templates from early payment templates. You can fine-tune the location of your user and/or workgroup templates folders but operate in view of that changes it for every Office programs, not just Word. Here are some examples of images from Internal Control Audit Report Template that you can get. If you desire to download it, just click the subsequent to image after that save. You can in supplement to transfer it to word or pdf and after that print your downloaded results. If you are looking for Internal Control Audit Report Template, you’ve come to the right place. We have some images not quite Internal Control Audit Report Template including images, pictures, photos, wallpapers, and more. In these page, we also have variety of images available. Such as png, jpg, full of beans gifs, pic art, logo, black and white, transparent, etc.